Platform
From Invisible to Invincible
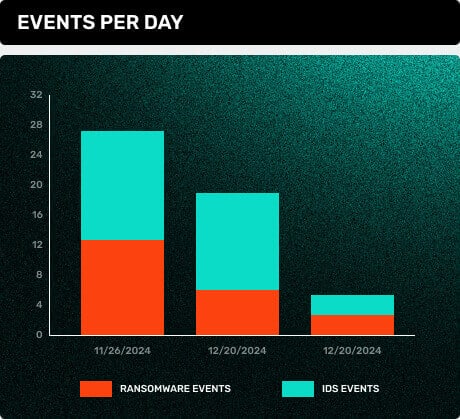
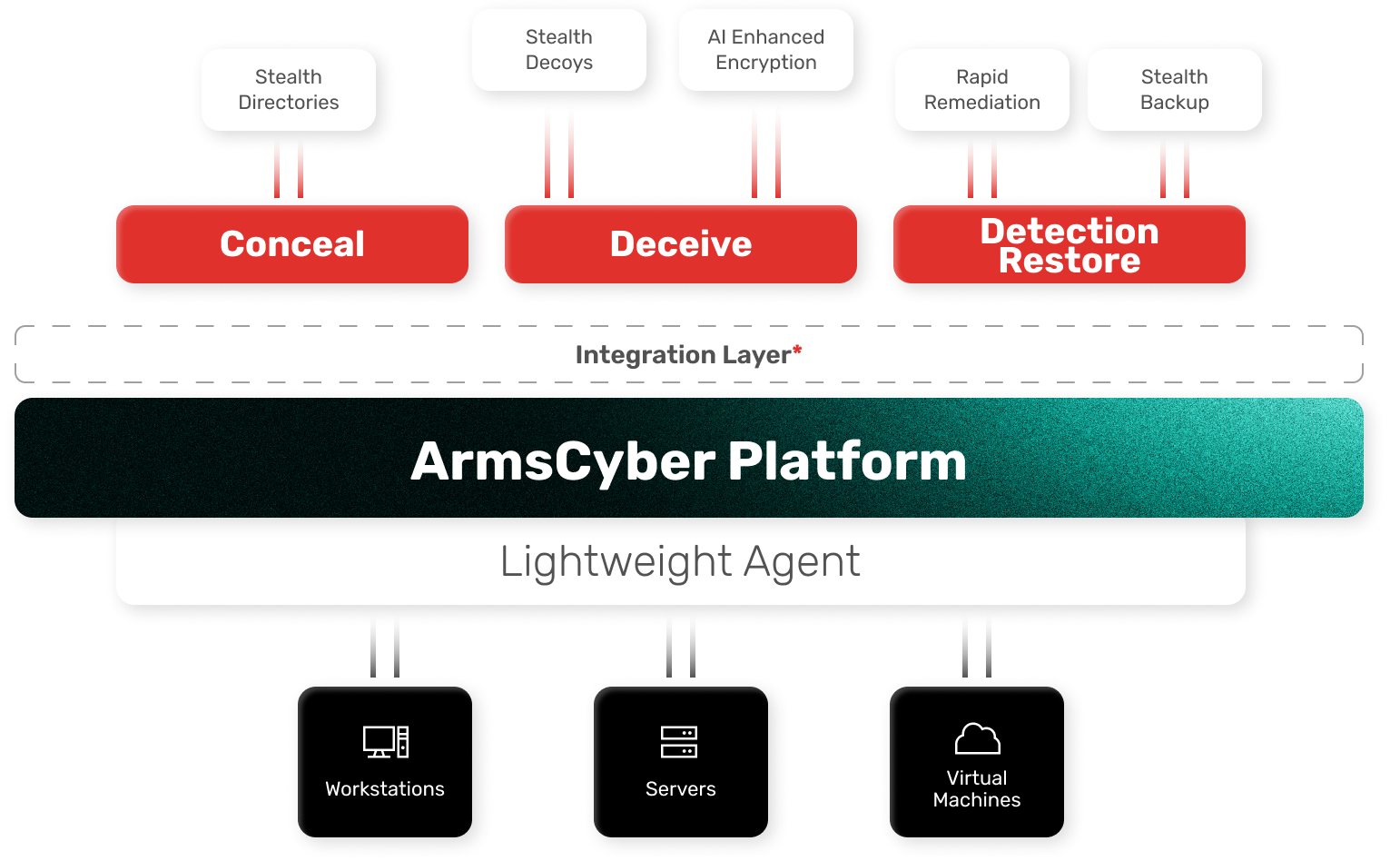
Stealth-Driven Ransomware Protection
Arms Cyber makes ransomware irrelevant by keeping your critical data invisible, stopping attacks before they spread, and ensuring no ransom payments, no public breaches, and no business disruption.