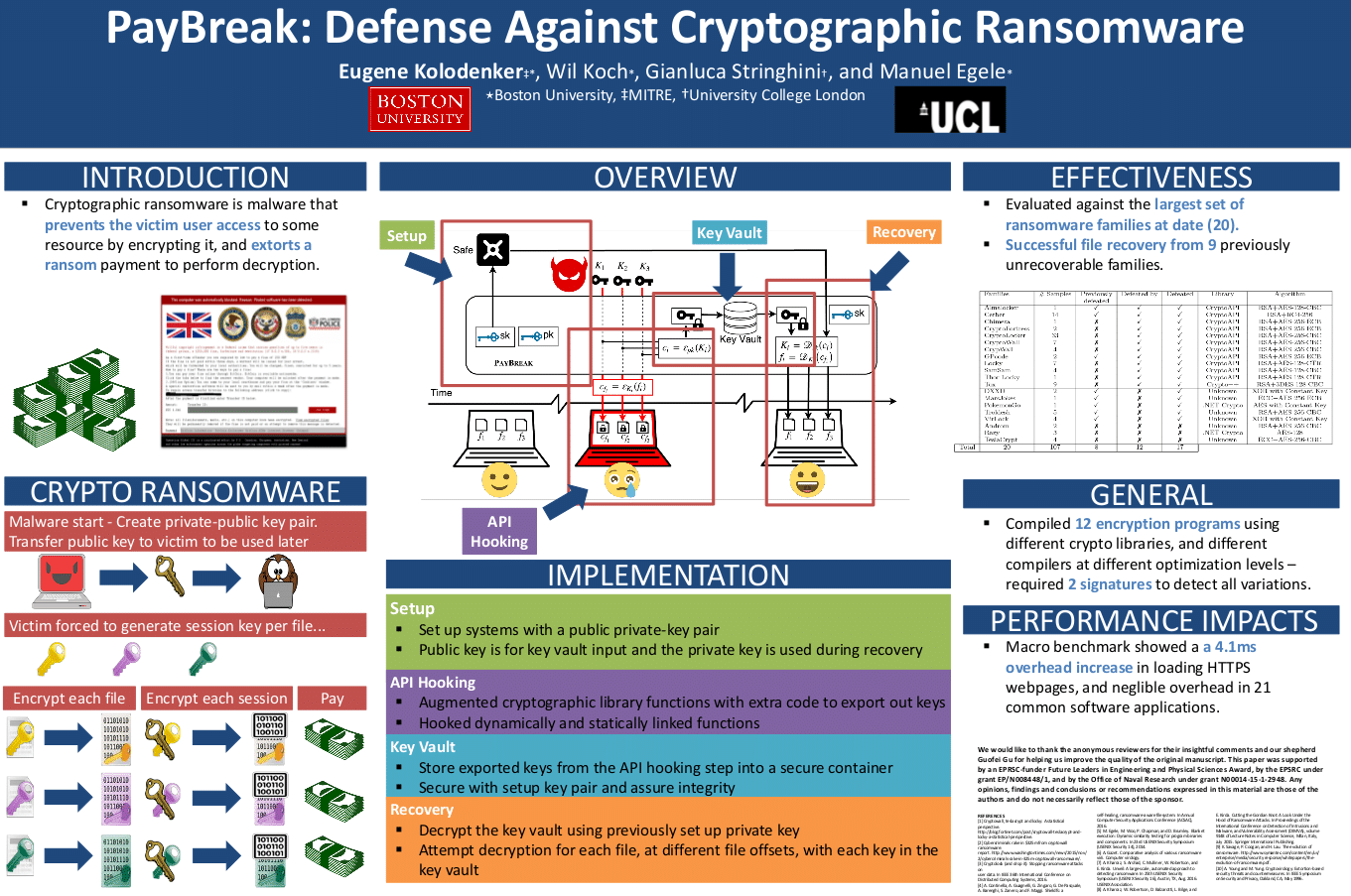
In the world of ransomware, DragonForce has emerged as a notable new player. First appearing in November 2023, the group quickly gained attention for its sophisticated attacks which leverage both technical skill and operational professionalism.
History
DragonForce ransomware stands out from the typical crop of ransomware groups due to its roots in a seasoned hacker community. The group’s name links it to the Malaysian hacktivist group, DragonForceMalaysia, though no definitive proof confirms a direct connection beyond this shared name. What we do know is that DragonForce operates with a level of professionalism that suggests they are not newcomers to the cybercrime scene.
One key to their rapid rise lies in their use of sophisticated tools, particularly those originating from other prominent ransomware groups. DragonForce has reportedly utilized the leaked code of LockBit 3.0, one of the most successful ransomware operations in history. (In 2022, the LockBit code was leaked, allowing numerous criminal groups, including DragonForce, to create customized ransomware without needing deep technical expertise.)
The leaked LockBit “builder” – essentially a toolset that allows criminals to generate personalized ransomware variants – has enabled DragonForce to escalate quickly, launching impactful attacks soon after its emergence. By using this builder, DragonForce not only fast-tracked its entry into the cybercrime world but also demonstrated an ability to deploy highly effective ransomware attacks.
Notable Attacks
Since its emergence, DragonForce has been responsible for several high-profile attacks, each targeting critical industries and organizations across the globe. The group’s first known attack targeted the Ohio Lottery in December 2023 and was particularly damaging, as the group claimed to have stolen over 600 GB of sensitive data, including personal information from lottery players and employees. According to reports, more than 1.5 million records were compromised, with details like names, email addresses, Social Security numbers, putting even financial winnings at risk. This attack was a clear demonstration of DragonForce’s ability to breach high-value targets and steal vast amounts of data.
Another significant incident occurred in March 2024 when DragonForce attacked the government of Palau, a small island nation. This attack was notable for the confusion it caused, as ransom notes from both DragonForce and LockBit were found on the affected systems, leading to speculation about whether the two groups were working together or if DragonForce was merely using the LockBit builder. Despite the government’s claim that no sensitive data was stolen, DragonForce insisted otherwise and threatened to leakover 21 GB of compromised files. This was one of several instances where DragonForce used double extortion—a tactic where hackers both encrypt data and threaten to leak it unless a ransom is paid.
A pattern of targeting government and critical infrastructure became more apparent with attacks on YakultAustralia, Elite Fitness in New Zealand, and Malone & Co, an accounting firm in Ireland. These organizations were not only targeted for ransom but also had their sensitive data exposed on DragonForce’s leak site, known as DragonLeaks. The leak site is where ransomware groups post stolen data if victims refuse to pay the ransom, a tactic designed to maximize pressure on the victim.
The frequency of DragonForce’s attacks has been concerning. Since its inception, DragonForce has claimed responsibility for nearly 30 victims in a matter of months. The range of industries—healthcare, finance, government, and even fitness equipment suppliers—demonstrates their versatility and opportunistic nature.
Professionalism in Cybercrime
One of the most striking aspects of DragonForce is how professional their operations appear to be. Cybersecurity experts have noted that the group runs its operation like a business, with clear communication protocols, structured ransom demands, and a high degree of organization. For example, DragonForce provides its victims with a “tree”—a list of the files they have stolen—to prove the breach and initiate negotiations. They also use TrueCrypt to encrypt the data on the victims’ servers, adding another layer of complexity to the recovery process. TrueCrypt is a software tool that encrypts files, making it nearly impossible to access the data without the correct decryption key.
DragonForce uses a Ransomware-as-a-Service (RaaS) model, where other criminals, known as affiliates, can use the ransomware to conduct their own attacks in exchange for a cut of the ransom. Affiliates receive around 80% of the ransom, while DragonForce keeps the remaining 20%. This model allows DragonForce to expand its reach without directly managing every attack. It also increases the frequency of attacks, as more affiliates get involved, meaning the group can simultaneously target multiple organizations.
Furthermore, the group offers its affiliates access to a control panel, which allows them to manage attacks in real-time. This tool automates many aspects of the attack process, making it easier for affiliates to launch and manage ransomware campaigns. By streamlining the attack process, DragonForce ensures that even less technically skilled hackers can participate, further expanding their reach.
The group’s professionalism is also evident in their negotiations. Unlike some ransomware gangs that rely solely on threats, DragonForce engages in lengthy discussions with their victims. For instance, in one leaked negotiation chat, the group patiently walked through the process of file decryption with the victim, allowing them to test a small sample of decrypted files before agreeing to a final ransom payment. This calculated approach not only builds a sense of trust between the attackers and the victims but also increases the likelihood of a ransom being paid.
DragonForce is also known for its reliance on automation. This reduces the need for human intervention and allows them to scale their operations more efficiently. Automation alsi makes it harder for cybersecurity defenses to keep up, as attacks can be launched quickly and in large volumes. Additionally, the use of automated systems means that the group can target multiple organizations simultaneously, increasing their overall success rate.
Conclusion
DragonForce ransomware is a potent example of the growing sophistication of cybercriminal organizations. With a foundation built on proven tools like the LockBit builder, a professional business model, and a calculated approach to extortion, DragonForce has quickly become a major threat in the world of cybersecurity. Their willingness to target a broad range of industries and their strategic use of double extortion and automation make them a formidable adversary.
While it remains to be seen whether DragonForce will continue to rise or eventually face the same law enforcement crackdowns that have dismantled other ransomware groups, their current operational model is efficient, profitable, and dangerous. Understanding how they operate is key for any organization looking to defend against this and other ransomware groups.
How Arms Cyber Can Help
The Arms Cyber ransomware solution employs a comprehensive, multilayered defense-in-depth approach that combats ransomware at every stage of execution. Utilizing a mix of cutting-edge strategies, traditional defenses are transformed into a moving maze, designed to disorient and effectively disrupt even the most advanced attackers. From initial intrusion, through attempts at evasion, to malicious payload execution, Arms Cyber identifies and neutralizes ransomware threats earlier and more effectively compared to signature-based and behavioral methodologies.