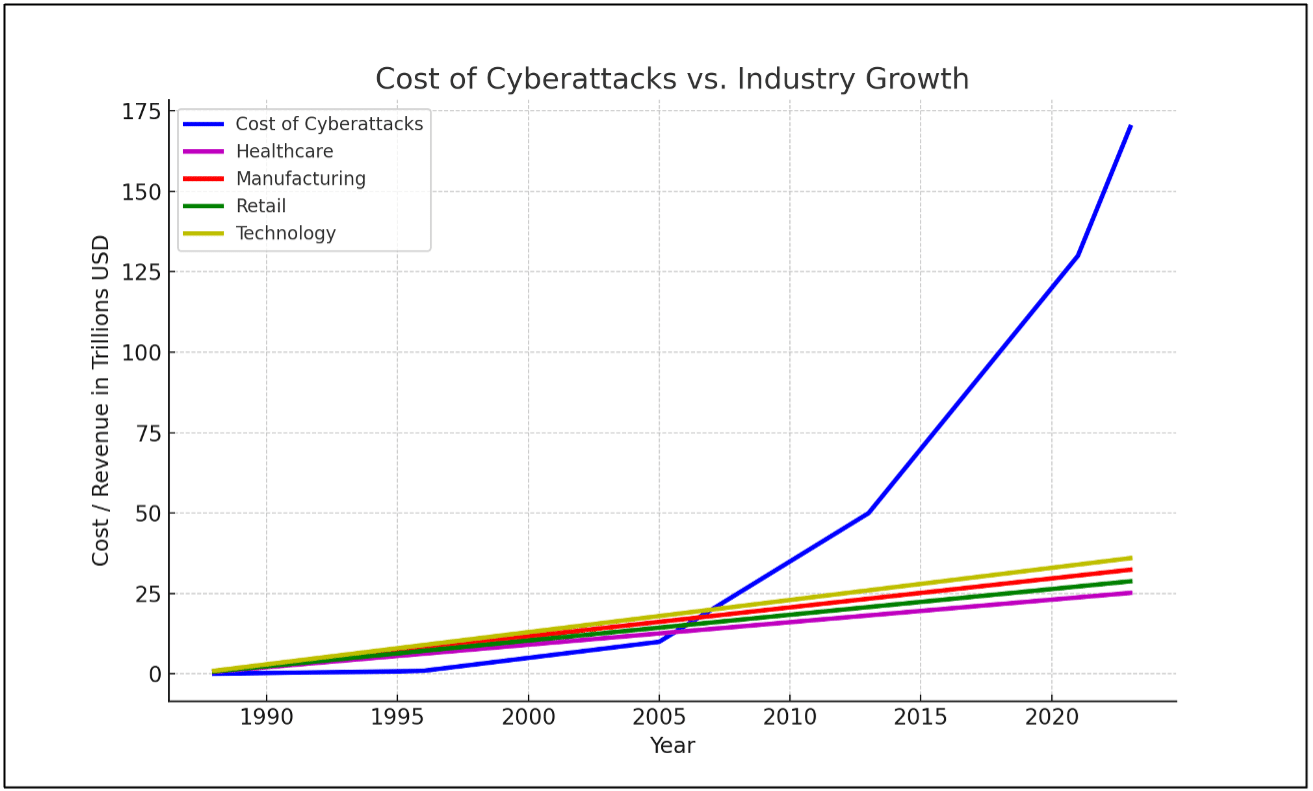
Having grown from $1.5 billion in 1999 to an astounding $8 trillion in 2023, the global cost of cybercrime now exceeds the GDP of Japan and generates more income than the top four global industries combined. Experts predict this will increase to $10.5 trillion annually by 2025 with an annual growth rate of 15% over the next five years.
By examining three key periods of explosive growth, we reveal pivotal moments in which cybercriminals overcame major barriers, fueling unprecedented expansion. Understanding this progression is critical to comprehending the breadth and difficulty of the problem and devising effective strategies to mitigate it.
The Early Days of Cybercrime
While cybercrime has been around since the birth of the internet, its earliest practitioners were often motivated by academic curiosity. The first major incident was the Morris Worm, created in 1988 by Robert Morris, a graduate student at Cornell University. Morris intended the worm as an experiment to understand the internet’s size and security flaws. Unfortunately, he miscalculated the virus’ replication rate and, within twenty-four hours of its release, “The Morris Worm” had infected ten percent of computers on the fledgling internet, degrading most and rendering many inoperable. The damage was considerable for the time, with estimates ranging from $100,000 to $10 million.
As an experiment, the Morris Worm was a complete success, highlighting the internet’s flaws and the need for increased security measures. But it also served as a proof of concept for cybercriminals, painfully demonstrating the potential of malicious code to cause widespread chaos.
The Birth of Cyber Extortion
A year later, in 1989, Joseph Popp, a Harvard-educated biologist got his hands on the mailing list for the World Health Organization’s AIDS conference and PC Business World Magazine and mailed 26,000 infected floppy disks to people in 90 countries. The unsolicited disk came with installation instructions and a fine-print license agreement stating that, by installing, the user agreed to pay a “mandatory leasing fee.” After 60 reboots, the virus, known today as the “AIDS Trojan” or “PC Cyborg,” encrypted files on victims’ computers and demanded payment be sent to a PO Box in Panama.
While this first known attempt at cyber extortion, the business model itself was completely ineffective The two leasing options translate to $480 and $962 in 2024 dollars. And 5.25” floppy disks were around $3.50apiece – that’s $232,000 today. Adding the cost of printing 26,000 sets instructions and license agreements, envelopes and international postage, and the effort clearly wasn’t worth the potential payoff. Popp would also have had to physically retrieve payments from the PO box, making him an easy target for law enforcement.
Attacks like Popp’s gave rise to signature-based antivirus (AV) software, which scans questionable files and compares them to a database of known malware. If the AV recognizes malicious activity, the file is not allowed to execute, preventing the attack. This became the primary method for detecting and removing computer viruses.
First Explosion: Antivirus Defeated
Without a safe way to receive direct payment, and AVs able to detect known malware, attackers shifted to phishing and other social engineering tactics, impersonating legitimate institutions through fraudulent emails and websites in order to harvest sensitive information and steal identities. They also began to use advanced techniques like polymorphic and metamorphic malware which change their code structure. No longer matching the signature of known malware, there were increasingly able to bypass AVs, leading to a 65% increase in cybercrime from 2004 to 2005.
One of the more notable incidents was the Citibank phishing scam, where attackers sent out fake Citibank emails which lead victims to a malicious website designed to capture their login details. This attack resulted in the theft of thousands of credentials and millions of dollars from unsuspecting customers. Likewise, the TJX data breach in 2007 exploited weak wireless network security to steal over 45 million credit and debit card numbers, resulting in an estimated $256 million in costs, settlements, and security upgrades. The polymorphic Storm Worm malware was active for years, ultimately infecting an estimated fifty million computers and shutting down internet access for hundreds of thousands of users.
The world of cybersecurity responded to these new threats by creating Endpoint Detection and Response (EDR) to fill the gap left by signature-based AVs. To this day a popular defense, EDRs, instead of scanning for known malware signatures, look for suspicious patterns of behavior and attack indicators. Activity that significantly deviates from the normal baseline is recognized and stopped, even if the malicious code itself doesn’t match a known signature.
Second Explosion: The Advent of Cryptocurrencies
When Bitcoin launched in 2009, cyber criminals finally had a secure, anonymous way to receive payments. The ability to bypass traditional financial systems meant less scrutiny and fewer regulations and lead to a 300% increase in the global cost of cybercrime between 2011 and 2014. The overall scope of attacks also increased significantly, with attacks like WannaCry and NotPetya causing billions of dollars in damage and disrupting global operations across critical sectors like healthcare, manufacturing and logistics
Cryptocurrencies also played a significant role in the rise of hostile nation-state actors and advanced persistent threats (APTs), enabling funding and execution of complex cyber operations with minimal risk of detection or tracking. Notable examples include Operation Aurora, in which Chinese hackers targeted Google and over 20 other companies from late 2009 to early 2010. This sophisticated cyber espionage campaign aimed to access and modify source code repositories at high-tech, security, and defense contractors. Another prominent example is the Sony Pictures hack in 2014, attributed to North Korean hackers. The breach led to the leak of vast amounts of confidential data, including employee information, emails, and unreleased films, causing severe financial and reputational damage to Sony. Overall, nation-state and APT cyber incidents increased 100% from 2017 to 2020 and have continued to steadily rise ever since.
At this point, the only thing stemming the tide of attacks was EDR’s ability to identify malicious behavior…
Third Explosion: Evasive Malware
…but the rise of evasive and fileless malware in the early 2020s allowed attackers completely bypass behavior-based security measures. Fileless malware, unlike traditional malware, does not rely on executable files to infect systems. Instead, it leverages legitimate tools and processes already present in the system, such as PowerShell and Windows Management Instrumentation (WMI). The malicious code doesn’t just look legitimate, it behaves legitimately too, making it significantly harder- if not impossible- for AV and EDR to detect and mitigate.
Notable attacks include the Sunburst attack in 2020, part of the SolarWinds compromise, where attackers injected malicious code into the SolarWinds Orion software update, impacting several U.S. government agencies and thousands of customers. This attack caused extensive damage, compromising approximately 18,000 SolarWinds customers and leading to significant data breaches at high-profile targets such as Microsoft, FireEye, and various U.S. federal agencies. The full extent of the damage is still being assessed, but it has been described as one of the most serious cyber-espionage campaigns ever detected. Also the DarkVishnya and Emotet attacks which caused hundreds of millions in losses to financial institutions around the world. Overall fileless malware attacks surged by 1400% in 2022 underscoring their effectiveness and the growing threat they pose.
A Call to Action: Strategic Level Solutions
Cybercrime has evolved from a virtually non-existent threat to the fastest-growing industry on the planet. This explosive growth underscores the urgent need for comprehensive strategies to combat the escalating threat.
Enhanced Regulations: Governments should implement and enforce stricter cybersecurity regulations. This includes mandating regular security assessments and compliance checks for businesses. By establishing a robust regulatory framework, governments can ensure that organizations adhere to the highest cybersecurity standards, reducing vulnerabilities and enhancing overall security.
Stringent Reporting Requirements: Post-attack reporting must be more rigorous, detailing what happened and which vulnerabilities were exploited. This transparency will help other organizations fortify their defenses against similar attacks. Comprehensive incident reporting will provide valuable insights into emerging threats and attack vectors, enabling the cybersecurity community to develop more effective countermeasures.
Defense-in-Depth Approach: The most robust defense strategy is a layered one. Organizations should adopt a defense-in-depth approach, which includes multiple layers of security controls throughout an IT system. This strategy ensures that if one layer fails, others remain to thwart an attack. By incorporating firewalls, intrusion detection systems, endpoint protection, and continuous monitoring, organizations can build resilient defenses capable of withstanding sophisticated attacks.
How Arms Cyber Can Help
The Arms Cyber ransomware solution employs a comprehensive, multilayered defense-in-depth approach that combats ransomware at every stage of execution. Utilizing a mix of cutting-edge strategies, traditional defenses are transformed into a moving maze, designed to disorient and effectively disrupt even the most advanced attackers. From initial intrusion, through attempts at evasion, to malicious payload execution, Arms Cyber identifies and neutralizes ransomware threats earlier and more effectively compared to signature-based and behavioral methodologies.